Security Analytics Engine
Detecting Threats in Real Time: Security Analytics Engine
With CANARIS SIEM, organizations can gain better visibility into their security posture improve compliance with industry regulations, and reduce the risk of financial and reputational damage from security incidents.

CANARIS SIEM offers advanced Security Analytics Engine that helps detect & prevent malware or any potential anomalies in the entire network.

This engine can identify patterns and anomalies that indicate potential security threats, and provide actionable insights to security teams.

Tool provides options to configure "Play Books" and offers Automated Response & Remediation measures.

Tool is designed in accordance with guidelines of PCI-DSS, HIPAA, GDPR, CIS & NIST to ensure compliance for Enterprises across the verticals.

Ability to ingest a large amount of log data coming from big, unrelated devices in a multi-vendor, multi-platform, multi-cloud environment.

IPs provide valuable insights into emerging and existing threats, enabling security teams to stay ahead of potential attacks.
SIEM (Security Information and Event Management) is a security solution that helps organizations collect, analyze, and respond to security events and incidents in real-time. The key features of SIEM include:


Detecting Threats in Real Time: Security Analytics Engine
Ensuring Compliance and Mitigating Risk: Audit and Policy Monitoring
Rapidly Identifying and Neutralizing Threats: Threat Detection & Response
Staying Ahead of Regulations: Regulatory Compliance Made Easy

Event monitoring and analysis

Incident detection and response

Threat Intelligence

Threat Hunting Security Analytics

Continual improvement of SOC operations

Provide forensic analysis support in case on any incident

Use Case engineering and new integrations to increase visibility

Integration of the solutions to provide a comprehensive single dashboard view of the securityrisks/ incidents for the bank
SIEM is used to collect, aggregate, index and analyze security data, helping organizations detect intrusions, threats and behavioral anomalies. As cyber threats are becoming more sophisticated,real-time monitoring and security analysis are needed for fast threat detection and remediation. That is why our light-weight agent provides the necessary monitoring and response capabilities, while our server component provides the security intelligence and performs data analysis.
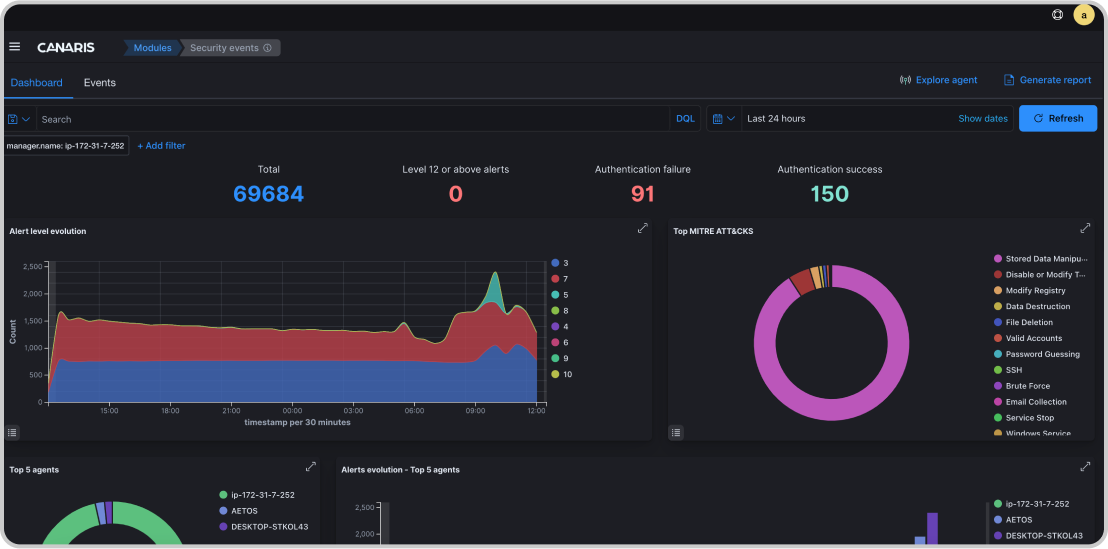
Canaris Siem is a security tool that can detect threats by analyzing activity on individual endpoints or hosts through a host-based intrusion detection system. It can identify known threats using rules and signatures, and also detect custom threats specific to the organization's environment. Siem has file integrity monitoring features to detect changes to critical system files or configurations. It provides real-time alerts and notifications to respond to potential threats quickly and investigate incidents. Siem is an effective tool to improve endpoint security and provide early warning of security incidents.
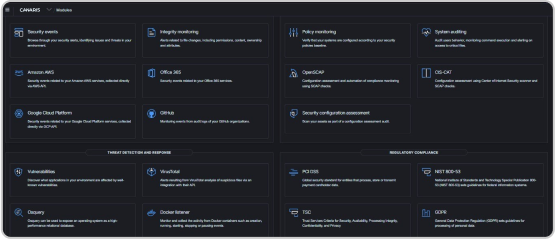
Siem is a security analytics platform that analyzes log data from various sources to detect and respond to security threats. It uses log analysis, file integrity monitoring, and host-based intrusion detection to provide comprehensive security analytics. Siem collects log data from endpoints through agents and provides pre-configured rules and signatures to detect known threats, as well as real-time alerting and notification capabilities for potential threats. Siem also includes file integrity monitoring features to detect changes to critical system files or configurations that may indicate a compromise.
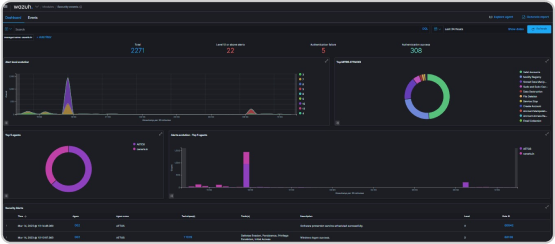
File Integrity Monitoring (FIM) is a security measure that detects unauthorized changes to critical system files and configurations. Siem, a security analytics platform, provides FIM capabilities using a combination of agent-based monitoring and signature-based detection to identify changes to files and configurations on endpoints. Siem's FIM rules and signatures cover a wide range of file types and configurations, and users can create custom rules to monitor specific files or configurations unique to their organization. Siem's FIM capabilities provide real-time detection of unauthorized changes, enhancing an organization's IT infrastructure security.
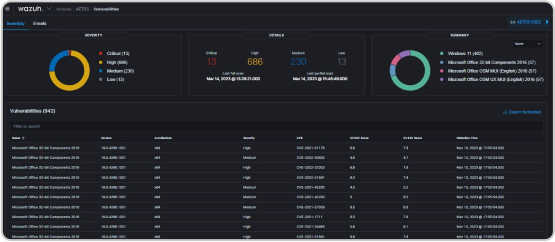
Siem is a security analytics platform that detects and addresses security vulnerabilities in an organization's IT infrastructure. It identifies potential vulnerabilities by analyzing logs from endpoints using vulnerability databases and correlating that information with known vulnerabilities and attack patterns. Siem has pre-configured and customizable rules to detect specific vulnerabilities or attack patterns. It provides real-time alerting and notification capabilities to respond to potential threats and investigate vulnerabilities. Siem also offers remediation guidance and integration with vulnerability management solutions to address potential security risks.

Configuration assessment involves analyzing an organization's IT infrastructure configuration settings to identify potential security risks. Siem is a security analytics platform that offers configuration assessment capabilities by collecting and analyzing configuration data from endpoints and correlating that information with known best practices and security policies to identify potential configuration issues. Siem's configuration assessment capabilities help organizations enhance the security posture of their IT infrastructure by identifying and remediating potential configuration issues.
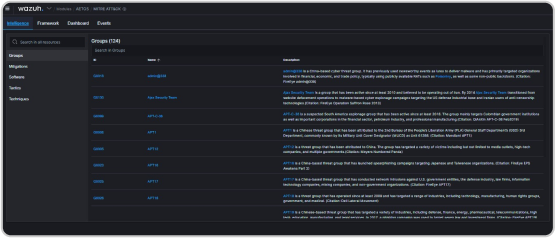
Siem is an open-source security analytics platform that offers incident response capabilities to help organizations respond to security incidents. It collects and analyzes log data, file integrity monitoring data, and other security-related events from endpoints. Siem provides pre-defined incident response procedures covering a wide range of incident types, including malware infections, system compromise, and data breaches. Siem's incident response capabilities include real-time alerting and notification, forensic analysis, and integration with incident response and remediation tools, enabling security teams to quickly respond to potential incidents, conduct detailed investigations, and streamline their incident response processes.
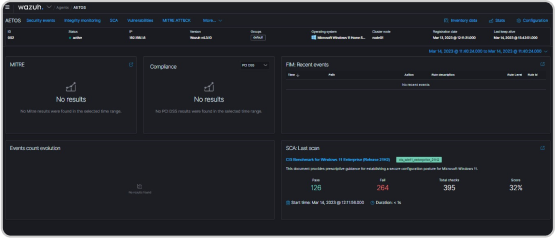
Siem is a security analytics platform that supports regulatory compliance by providing pre-configured rules and signatures to detect security events relevant to industry regulations and standards like PCI DSS, HIPAA, and GDPR. It also enables organizations to create custom rules and policies to meet their specific compliance needs, avoiding legal and financial penalties and maintaining their reputation.
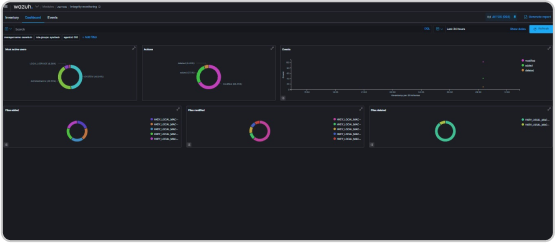
SIEM is a security analytics platform that can protect cloud-based resources and data from unauthorized access and other security threats. It offers real-time monitoring, threat detection, compliance monitoring, and automated incident response workflows. SIEM can integrate with popular cloud platforms and monitor cloud-related log data and security events, as well as monitor cloud-based infrastructure as code templates and configurations. Its cloud security capabilities can help organizations enhance their cybersecurity posture as they move their operations to the cloud.
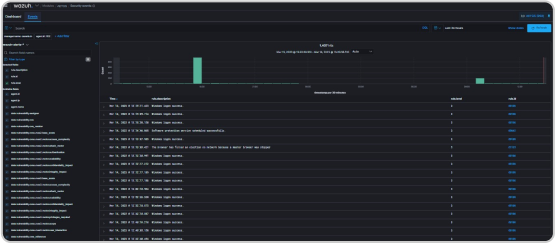
SIEM is a security analytics platform that enhances container security by monitoring container-related log data and security events, detecting potential security risks, providing real-time alerting and notification, and file integrity monitoring for container images. It can integrate with popular container orchestration platforms like Kubernetes and Docker Swarm, providing visibility into container environments and automating incident response workflows to help mitigate security threats.
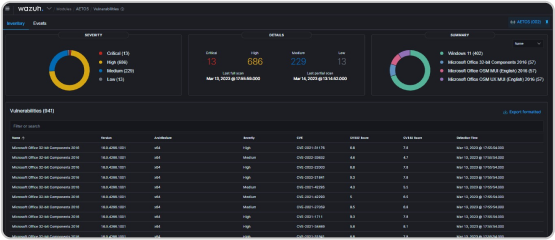

provides real-time monitoring, correlation and expert analysis of activity in your environment, detecting and alerting on valid threats to your data and devices

Integrity Monitoring task is designed to track actions performed with the files and directories in the monitoring

Amazon AWS Security events are related to Amazon AWS services. Collected directly via Amazon API

Security events are related to Google cloud platform services. Collected directly via GCP API

Integrity Monitoring task is designed to track actions performed with the files and directories in the monitoring

Security events related to office 365 1.Changes to important roles -who have successfully compromised a user account will do what they can to elevate their privileges by acquiring more roles
Compliance in cybersecurity is essential because it helps to ensure that organizations are following best practices in protecting their sensitive data. It also helps to prevent cyber attacks, data breaches, and other security incidents that can result in financial losses, repetitional damage, and legal liabilities.

RBI, NABARD Guidelines

OWASP
Framework

PCI-DSS

MITRE ATT&CK

GDPR
Reach out to us, WE CAN MAKE SOMETHING GREAT TOGETHER
113, 1st floor, Sai Vision Complex, Pimple Saudagar, 411027 Pune
[email protected]
+91-98600 38144
Mon-Sat: 9AM - 6PM
For all enquiries, please email us on the form below